Smart detection across every security layer
Physical security faces growing challenges today. Critical infrastructure such as data centers, industrial sites, airports, or government buildings must not only be reliably protected against unauthorized access, but also operated efficiently, in compliance with data protection regulations, and with minimal disruption to daily operations. Individual security measures quickly reach their limits in this context: perimeter sensors, video surveillance, or access control systems are each designed for specific scenarios and, on their own, do not provide continuous protection from the outer perimeter through to sensitive interior areas.
To address these challenges, multi-layered security concepts adopt a holistic approach. Sites, buildings, and particularly sensitive zones are divided into multiple, interconnected security areas that build upon one another. Each area represents a distinct layer of protection with specific requirements for detection, alerting, and response. The goal is to identify threats as early as possible, reduce false alarms, and trigger security measures in a targeted and effective way.
What does “multi-layered security” mean in physical security architecture?
The term multi-layered security is widely used in the security industry, but it is not defined in a uniform way. While it is well established in IT and cybersecurity, it is becoming increasingly relevant in the context of physical security. At its core, a multi-layered security concept describes a spatial, layered model of protection:
- The site is divided into multiple security areas, progressing from the outside inward.
- Each zone addresses different risks and potential vulnerabilities.
- Access to a higher security level is only possible via the preceding one (often referred to as the shell principle or onion model).
- Events from different zones and technologies are centrally aggregated and evaluated, for example within a security platform such as a VMS or PSIM.
This interaction of multiple protective layers increases the overall resilience of the security architecture: even if one layer is breached, additional layers remain in place to detect and respond to threats.
Typical security layers in a multi-layered security concept
A multi-layered security concept is typically structured into several clearly defined layers. The closer a potential threat moves toward critical core areas, the higher the requirements for precision, reliability, and alarm quality become.
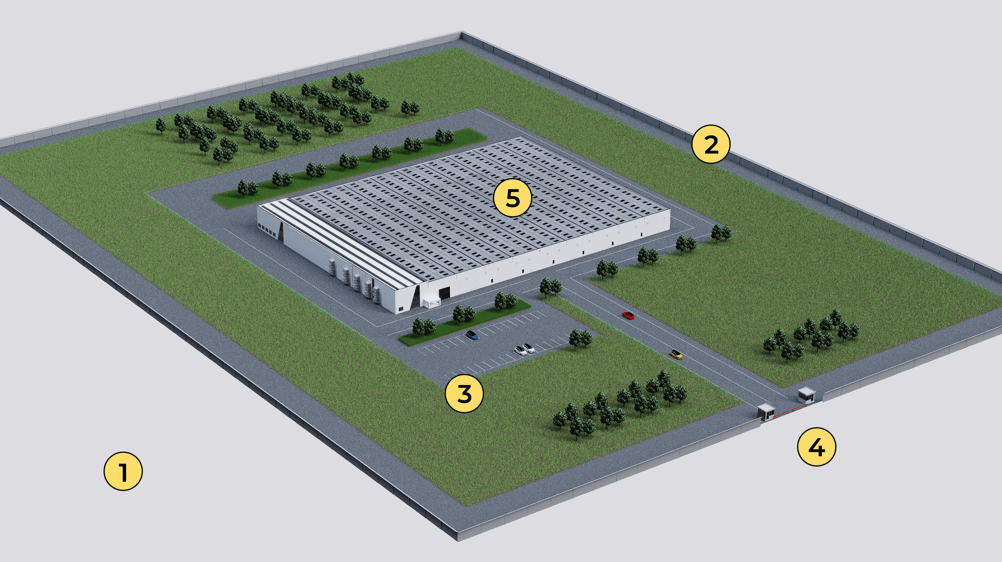
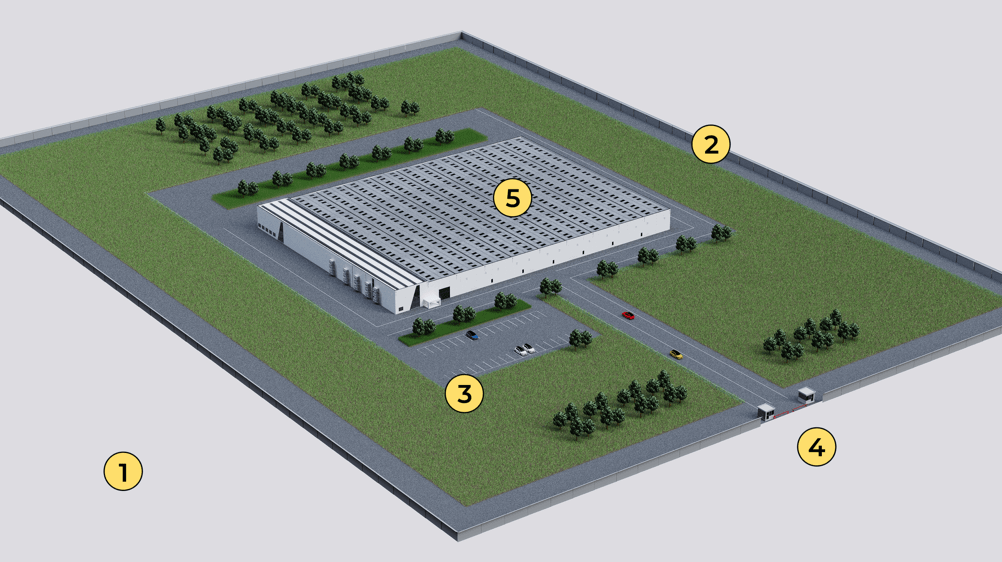
Exemplary overview of a multi-layered security concept:
- Approach zone
- Perimeter boundary
- Open area between perimeter and building
- Gates and access points
- Building facade
1. Approach zone: early threat detection
The approach zone forms the outermost layer of a multi-layered security concept. It is deliberately located outside the actual perimeter and follows a clear objective: to make potential threats visible as early as possible, and before critical areas are reached.
At this stage, the focus is less on immediate alarming and more on situational awareness and context. Detecting approaching individuals or vehicles at an early point gives security personnel valuable time for initial assessment, alarm verification, or preventive measures.
At the same time, this zone places particularly high demands on detection capabilities. Large outdoor areas, changing environmental conditions, and public spaces require monitoring solutions that can reliably distinguish relevant events from everyday movement without generating unnecessary alarms or violating data protection requirements.
A well-designed approach zone is therefore the foundation for a proactive and forward-looking security strategy.
2. Perimeter boundary: Protecting the physical barrier
While the approach zone primarily focuses on early detection, the perimeter marks the point at which a potential threat can turn into a concrete security incident. Fences, walls, or other physical barriers define the visible boundary between public space and protected premises.
At this security layer, the focus shifts from observation to the clear detection and assessment of boundary violations. Movement along the perimeter line, approaches to the fence, or attempts to breach the barrier must be reliably detected and localized. What matters is not every movement as such, but its context: Is it a random approach, an environmental influence, or a deliberate intrusion attempt?
Effective perimeter protection therefore provides precise information about where and how an event is occurring. This clear localization forms the basis for a rapid response, whether by security personnel, automated processes, or escalation to higher-level security and alarm systems.

3. Open area between perimeter and building
Once the perimeter has been breached, the focus shifts from boundary protection to active site control. The open area between the outer barrier and the building structure serves as a critical transition zone: it is here that a security incident is either brought under control at an early stage or allowed to escalate unnoticed.
In this zone, transparency is key. Movements must not only be detected, but also remain traceable across the site. An individual or vehicle detected at the perimeter should be continuously tracked after the breach, regardless of pathways, terrain layout, or the viewing direction of individual sensors.
This creates consistent situational awareness for security personnel: Where is the object currently located? How is it moving? In which direction is the situation developing? This spatial context is essential for initiating targeted measures and verifying alarms.
Especially on large or complex sites, the importance of this security layer becomes evident. It connects perimeter protection and building security into a continuous monitoring concept, significantly improving response capabilities across the entire premises.
4. Gates and access points
In addition to free movement across the site, potential access points inevitably narrow down to defined transition points. Gates, access roads, and barriers concentrate traffic flow and therefore present a particular security challenge: they must remain open enough to support regular operations while clearly restricting unauthorized access.
Unlike the perimeter boundary, these points are no longer about simple detection, but about controlled access. Movement is generally permitted here, but only in the expected direction, at the right time, and for authorized objects. Security-relevant incidents often arise not from the presence of movement itself, but from deviations from the expected process.
Effective protection of gates and access points therefore does not only detect that someone is moving, but how and where. Attempts to bypass barriers, use incorrect driving directions, or pass through access points outside the intended passage must be reliably detected without unnecessarily disrupting normal traffic flow.
5. Building facade: the final outer barrier
As a threat reaches the building structure, the security situation intensifies once again. What was previously movement in an outdoor environment now becomes an immediate risk to protected interior areas. At the same time, the window for response narrows significantly: events at the facade leave little room for delay or misinterpretation. The building facade therefore represents the final outer barrier and marks the transition from site monitoring to building protection.
At this security layer, the focus shifts to the immediate proximity of the building structure (facades, windows, doors, and roof areas) and to the analysis of movement in direct relation to the building itself. Of particular relevance are behaviors that indicate climbing, intrusion, or tampering.
At the same time, the environment is especially demanding. Weather conditions, moving vegetation, or changing lighting directly affect the facade and must not lead to false interpretations.
Effective facade protection is therefore defined by precision and robustness. It reliably detects security-relevant activities at the point where they become critical and acts as a selective filter: only confirmed, relevant events are passed on to the next escalation level.
In addition: Protection of sensitive interior areas and assets
As security shifts from the exterior to the interior, the focus of physical protection changes fundamentally. It is no longer about monitoring large areas, but about safeguarding clearly defined, sensitive zones.
Inside buildings, this typically includes restricted access points, or specific valuable assets, server rooms or technical areas. Security measures in these spaces must operate without disrupting daily operations, while movements within the area must be reliably detected and accurately interpreted. Volumetric sensing, precision, and data privacy are key considerations.
Particularly critical are individual assets that must remain protected even as adjacent areas stay accessible, for example during maintenance of server racks or machinery. Even the smallest movement, such as a hand approaching a restricted zone, must be detected with absolute reliability.
Connecting security layers through technology
At first glance, a multi-layered security concept may seem highly complex: multiple zones, different sensors, countless events – and seemingly more work for security personnel. In practice, however, the effort is not determined by the number of layers, but by how well the technologies employed work together.
Modern security architectures therefore rely on systems that consolidate information from various layers, contextualize it, and selectively pass it on. Instead of isolated individual alarms, a continuous situational picture emerges – one that prioritizes relevant events and avoids unnecessary escalations. For security staff, this means less manual evaluation and greater confidence in decision-making.
3D LiDAR technology has proven to be a powerful complement in this interplay. It operates independently of lighting and weather conditions, provides precise spatial object data, and enables anonymous detection.
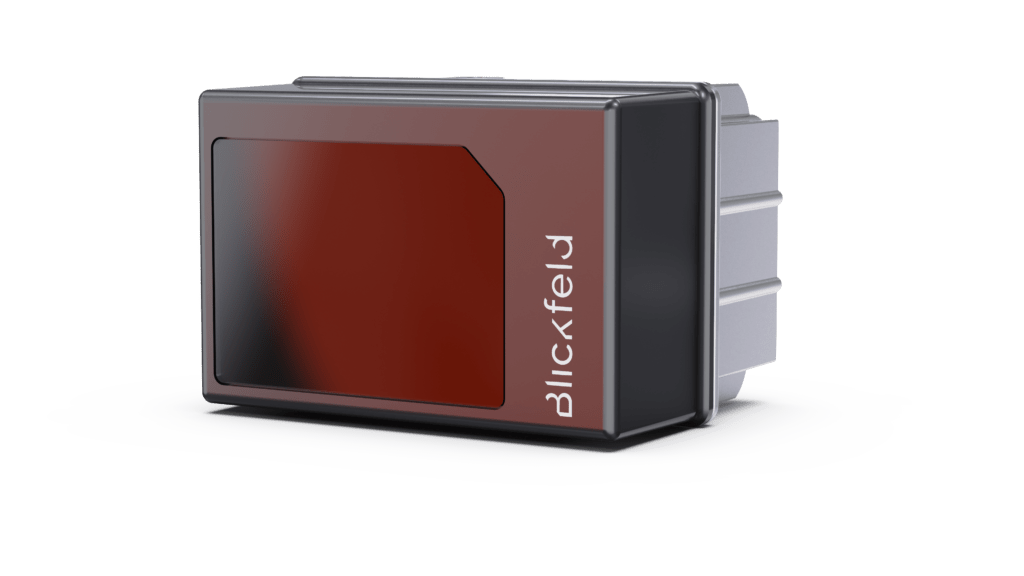
Integrating 3D LiDAR into multi-layered security
Smart 3D LiDAR sensors, such as QbProtect, can be deployed across multiple security layers – from the approach zone and perimeter to the building facade, interior areas, and asset protection. Software-configurable detection, flexible security zone placement, and on-device data processing allow detection and alarm behavior to be precisely tailored to each security layer. By collecting only anonymous 3D data, QbProtect ensures that no conclusions can be drawn about individuals in the monitored area, making it compliant with data protection regulations.
Conclusion: Smarter security through layered design
Multi-layered security concepts provide a structured, practical approach to physical protection in modern facilities. What matters is not the number of layers, but how intelligently they are interconnected. Flexible technologies provide a way to connect diverse security requirements and create a cohesive, effective defense strategy.